HTTP Message Methods - Part 2 of Chapter 3 from HTTP: The Definitive Guide (4/4)
[previous] |
HTTP: The Definitive Guide, Chapter 3: HTTP Messages
DELETE
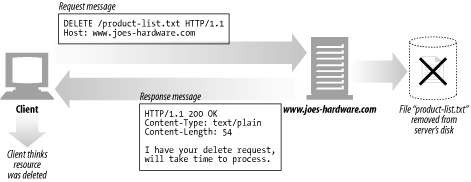
The DELETE method does just what you would think--it asks the server to delete the resources specified by the request URL. However, the client application is not guaranteed that the delete is carried out. This is because the HTTP specification allows the server to override the request without telling the client. Figure 3-13 shows an example of the DELETE method.
Extension Methods
HTTP was designed to be field-extensible, so new features wouldn't cause older software to fail. Extension methods are methods that are not defined in the HTTP/1.1 specification. They provide developers with a means of extending the capabilities of the HTTP services their servers implement on the resources that the servers manage.Some common examples of extension methods are listed in Table 3-5. These methods are all part of the WebDAV HTTP extension (see Chapter 19) that helps support publishing of web content to web servers over HTTP.
Table 3-5: Example web publishing extension methods
Method | Description |
|---|---|
LOCK | Allows a user to "lock" a resource--for example, you could lock a resource while you are editing it to prevent others from editing it at the same time |
MKCOL | Allows a user to create a resource |
COPY | Facilitates copying resources on a server |
MOVE | Moves a resource on a server |
It's important to note that not all extension methods are defined in a formal specification. If you define an extension method, it's likely not to be understood by most HTTP applications. Likewise, it's possible that your HTTP applications could run into extension methods being used by other applications that it does not understand.
In these cases, it is best to be tolerant of extension methods. Proxies should try to relay messages with unknown methods through to downstream servers if they are capable of doing that without breaking end-to-end behavior. Otherwise, they should respond with a 501 Not Implemented status code. Dealing with extension methods (and HTTP extensions in general) is best done with the old rule, "be conservative in what you send, be liberal in what you accept."
[previous] |
Created: January 21, 2003
Revised: January 21, 2003
URL: https://webreference.com/programming/http/chap3/2/4.html


 Find a programming school near you
Find a programming school near you